In this article let’s have a look at things to consider during SSL certificate renewal in Exchange 2010 and 2013 environment.
First we need to confirm what type certificate we are using, i.e., the third-party certificate or self-signed certificate. And then we need to check the existing 3rd party certificate is associated with what all exchange services, number of SAN entries we have and note down them.
Let’s see the procedure of renewing the certificates for third party and self-signed.
For Third party Certificate Renewal
For renewing the third-party certificate, we need to apply a new certificate request from the third-party CA, then import the certificate to the Exchange servers and enable the related service (IIS, IMAP, POP, and SMTP) on the Exchange servers.
Follow the below steps:
Step 1: Obtain an SSL certificate. Purchase an SSL certificate from a well-known certification authority (CA).
Step 2: Generate and submit the certificate request: create a new certificate request for Secure Sockets Layer (SSL) services.
- Open Exchange Management Shell
- Run the following command, replace domain name and friendly name with your domain name and display name, and then run below command:
New-ExchangeCertificate -GenerateRequest -SubjectName “C=US, S = Contoso, L = Toybox, O = Test, OU = IT, CN = mail.contoso.com” -domainname mail.contoso.com, Mail.ad.contoso.com, Webmail.contoso.com -FriendlyName mail.contoso.com -privatekeyexportable:$true -path c:\cert.txt
IMP Note:
“DomainName” is used to populate one or more domain names (FQDNs) or server names in the resulting certificate request. We can replace ‘domainname’ according to our own environment.
“FriendlyName” is used to specify a display name for the resulting certificate. The display name must be lesser than 64 characters.
In SubjectName property, we can use the proper subject name by our own environment: c for country/region name, o for organization name and cn for common name.
- Submit the request to the certification authority and have the CA generate the certificate
Step 3: Enable the certificate on the Default Web site after your certificate has been generated, you must import it and then enable the certificate on the Default Web site.
- From the computer where step 2 was run, import the certificate. To import the certificate, open EMS and run the below cmdlet:
Import-ExchangeCertificate -path c:\cert.cer
Note: “c:\cert.cer” is the location and name of our certificate in my example.
- Copy the thumbprint of the certificate, which is the digest of the certificate data.
- Enable the certificate on the Default Web site, run the cmdlet in EMS and paste the copied thumbprint to the following cmdlet:
Enable-ExchangeCertificate -thumbprint <copied thumbprint value> -services “IIS,IMAP,POP,SMTP”
Note: Using the “enable-ExchangeCertificate” cmdlet will update the certificate mapping and replace the existing certificate that is configured in IIS, IMAP4, POP3, SMTP.
Step 4: Require the Client Access server virtual directories to use SSL
Step 5: Perform an IIS reset. Try browsing OWA and see if you get any errors
For Self Signed Certificate Renewal
For renewing the self-signed certificate, we need to get the old Thumbprint property of the expiring self-signed certificate, and then use New-ExchangeCertificate to renew the certificate and then enable the related service to the new certificate.
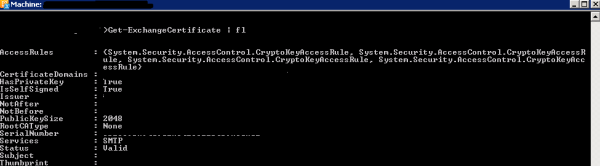
To get the existing thumbprint value
Run
Get-Exchangecertificate | fl
Important thing to note down the self-signed certificate should have a value True in the column IsSelfSigned
Then use the command remove-Exchangecertificate to remove the old expired certificate
Example
Remove-ExchangeCertificate -Thumbprint 5113ae0233a72fccb75b1d0198628675333d010e
You can use the command New-ExchangeCertificate to create a new certificate
Run the below command to perform the action
New-ExchangeCertificate -FriendlyName “SelfSigned Certificate” -KeySize 2048 -SubjectName “c=IN, s=, l=, o=CONTOSO, ou=IT, cn=CONTOSO.COM” -DomainName MAIL.CONTOSO.COM, AUTODISCOVER.CONTOSO.COM -PrivateKeyExportable $True
Below are the important things to keep in mind:
- You can assign only one certificate to the Default Web site at a time. I would recommend deleting the old certificate as it is useless and will create confusions because it will not be used by any services once we assign the new certificate.
- Ideally it should break or bring own any services while installing the new certificate. However, we may need to do an IISreset (not always but we may need it). So for few seconds till your IIS comes back we will experience a disconnection for few seconds
- Certificates cannot be changed after they are signed, otherwise they would provide no security. Once issued, a certificate holds all SANs. This means that a certificate would have to be revoked and a new one has to be issued to add a new SAN.
- You should first find out which names you want to register, because revoking and reissuing will most likely cost extra money. And also adding SAN entries will cost you extra money. If you have edge servers then the new certificate created must be imported on them and new edge subscription must be created.
- When you order a Unified Communications Certificate from a third party you can secure all the SAN names you need with one easily manageable certificate. After your Multiple Domain (UCC) SSL certificate is issued, you can add or remove Subject Alternative Names (SANs) at any time. SANs are the additional, non-primary domain names secured by your UCC SSL certificate. However, keep in mind: Changing your SANs generates a new certificate, which you must install on your server. Your old certificate only remains valid only for 72 hours and has to be replaced with new entries.
- Public trusted CA’s shall not issue a certificate with an Expiry Date later than 1 November 2015 with a SAN or Subject Common Name field containing a Reserved IP Address or Internal Server Name. As from 1 October 2016, CAs shall revoke all unexpired Certificates.
- If you are a server admin using internal names, you need to either reconfigure those servers to use a public name, or switch to a certificate issued by an internal CA before the 2015 cutoff date. All internal connections that require a publicly-trusted certificate must be done through names that are public and verifiable (it does not matter if those services are publicly accessible).
What things comes under internal name ?Any server name with a non-public domain name suffix. For example, http://www.contoso.local or server1.contoso.internal.
NetBIOS names or short hostnames, anything without a public domain. For example, Web1, ExchCAS1, or Frodo.
Any IPv4 address in the RFC 1918 range.
Any IPv6 address in the RFC 4193 range.
Thanks
Sathish Veerapandian
MVP – Exchange Server
Tagged: certificate request, self-signed certificate, SSL certificate


Quality articles is the main to attract the viewers to go
to see the website, that’s what this web page is providing.
LikeLike
Thanks for your comments 🙂
LikeLike
Everything is very open with a cleaqr clarification of the challenges.
It was really informative. Your site is useful. Many thanks for sharing!
LikeLike
Your are welcome 🙂
LikeLike
This post presents clear idea designed for the new visitors of blogging, that genuinely how
to do blogging and site-building.
LikeLike
Thanks for your comments !!!
LikeLike