Reverse NDR attack is one of the most common method of spamming a mail server by the hackers. Even though if they are unable to compromise any user accounts by this method in an organization they can increase the load on the messaging system and our network bandwidth by bouncing the NDR’s back and forth. This makes the end users more annoying to think why they got NDR’s for the message which they never sent.
What is Reverse NDR Attack?
1) Spammer creates and email address with the spam victim’s address in the sender field since sender can always be anonymous and in the recipient he addresses them with random common names at your domain.
Ex: from:Sathish@contoso.com , To:Jack@exchangequery.com,Jim@exchangequery.com
2) He attaches an spam email and sends to the random addressed recipients of the victims domain.
3) Your mail server cannot deliver the message and sends an NDR email back to what appears to be the sender of the original message, the spam victim.
4)The return email carries the non-delivery report and possibly the original spam message. Thinking it is email they sent, the spam victim reads the NDR and the included spam.
Microsoft has brought some basic filtering setup for this Backscatter detection in EOP(Exchange Online Protection) which is more beneficiary. It uses a method called BATV( Bounce Address Tag Validation)
What is BATV ?
BATV( Bounce Address Tag Validation) is a standard internet draft of validating a reverse NDR email to see whether it is legitimate with a tag value or not.
How does this works ?
It uses a cryptographic hash. This cryptographic hash contains a valid return path of an email address, time stamp in the encoded format.So any NDR that is returned to a system without this cryptographic has tag value will be halted/rejected and hence no bounce backs.
BATV replaces an envelope sender like sathish@hotmail.com with prvs=tag-value=sathish@hotmail.com, where prvs, called “Simple Private Signature” . This PRVS is one of the possible method of tagging the values though there are few more in the standards followed.
This cryptographic token cannot be forged at any cost until they come to know the PRVS tag value.
For on-premise setup If you have this reverse NDR filtering setup in your anti-spam filtering agent you need not worry about this setup since your spam filtering will take care of this part.
If you are an on-premise customer and if you have your email filtering with EOP then Microsoft recommends to turn on this feature .
If your Mailboxes are hosted with Office 365 you no need to worry about turning on this feature. However Microsoft recommends to turn this feature ON if your outbound email goes through Office365(Not sure why)
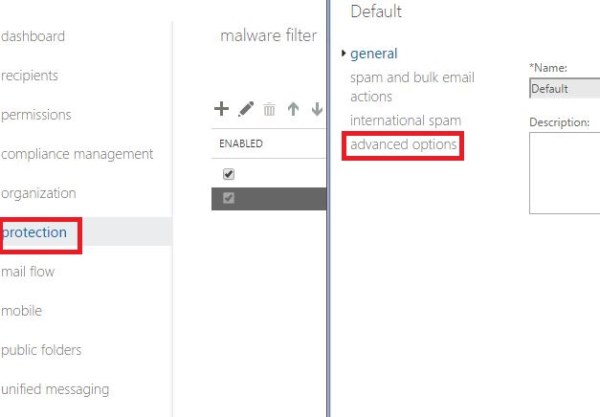
Below are the steps to turn on this feature in through EAC
Open EAC – Click on protection – Navigate to your Policy – Click Advanced
Turn on the NDR back scatter option
Enabling this option will definitely add additionally layer of security especially for reverse NDR attacks. Hope this helps.
Thanks
Sathish Veerapandian
MVP – Exchange Server
Tagged: NDR



Leave a comment