In the current scenario most of the Organizations are running Teams Room systems as their meeting room solution from their Offices. Few of their customers, vendors and partners host their meetings from Zoom ,WebEx or other meeting solutions. In these unique circumstances, we will be hitting in a scenario where there are people attending the meetings from Teams Room from our organization and the meeting sent by vendor or a customer might be Web-Ex or Zoom.
Knowing this requirement Microsoft released a supported Teams App version in the mid of last year for the Room Systems to join Cisco WebEx Meetings from a Teams enabled room system with the direct guest join. Later this option was extended to attend a Zoom Meetings as well from the Teams App version 4.6.20.0. We’ll walk through the procedures to enable Teams Room Devices to join the 3rd party meetings Cisco WebEx and Zoom Meetings.
There are few prerequisites to be met in order to join WebEx and Zoom Meetings from a Teams Room System
- Make sure the WebEx and the Zoom Meeting URLs are fully whitelisted in your proxy and in your network to fully support this scenario.
- Configure Office 365 Threat Protection and Link Rewrite exclusion list for WebEx and Zoom Meeting URLs.
- Configure your Room Mailbox to automatically accept and process the invitation from Zoom and WebEx.
- Configure this settings in your Room Systems devices , so that they are ready for this functionality.
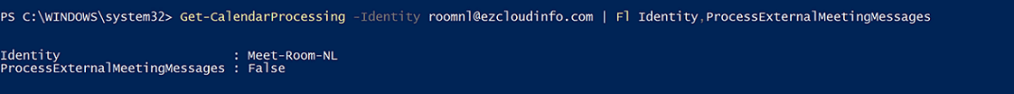
To make this work for the Room Mailbox Connect to your Office 365 Exchange Online Tenant and check for the current setup for accepting the meeting room from a 3rd party meeting invites by running the below command.
Get-CalendarProcesing -Identity UserPrincipalNameOfRoomMailbox | Fl Identity,ProcessExternalMeetingMessages
In our case the value is set to false which is by default. The ProcessExternalMeetingMessages parameter specifies whether to process meeting requests that originate outside the Exchange organization.
Run this command on the Room Mailbox of the Room System to accept meeting requests from Zoom and WebEx
Set-CalendarProcessing roomnl@ezcloudinfo.com -ProcessExternalMeetingMessages $True -DeleteComments $False -DeleteSubject $False

Now we could see that the value ProcessExternalMeetingMessages is set to True
Continue reading