Digital Operational Resilience Act (DORA) is reshaping how EU financial entities manage ICT risk, resilience testing, incident reporting, and third‑party risk. If you run Microsoft 365, Microsoft Purview Compliance Manager gives you a practical way to translate DORA requirements into actions, evidence, and measurable progress. This guide walks through a clean, step‑by‑step implementation flow from setting up a DORA assessment to assigning improvement actions and tracking your score, so you can be audit ready without drowning in spreadsheets.
Why use Microsoft Purview Compliance Manager for DORA ?
- Prebuilt assessments: DORA assessment templates map regulatory articles to actionable controls you can assign and track.
- Control mapping: Microsoft‑managed baselines and customer‑managed controls provide clarity on shared responsibility.
- Improvement actions: Structured tasks with owners, due dates, and recommended steps create accountability.
- Evidence management: Centralized artifacts (documents, links, screenshots) simplify audit preparation.
- Real‑time scoring: Compliance scores help prioritize high‑risk gaps and demonstrate progress.
Prerequisites and approach
- Access: Ensure you have appropriate roles in Microsoft Purview (e.g., Compliance Manager Admin or similar).
- Scope: Decide which services to cover first; start with Microsoft 365 for a focused rollout.
- Vanilla setup: Use a fresh assessment group to avoid inherited noise and control drift.
Quick Tip
Can also use the default user access options available from the Assesment option in the Compliance Manager Portal
Step‑by‑step setup in Compliance Manager
Create and configure your DORA assessment
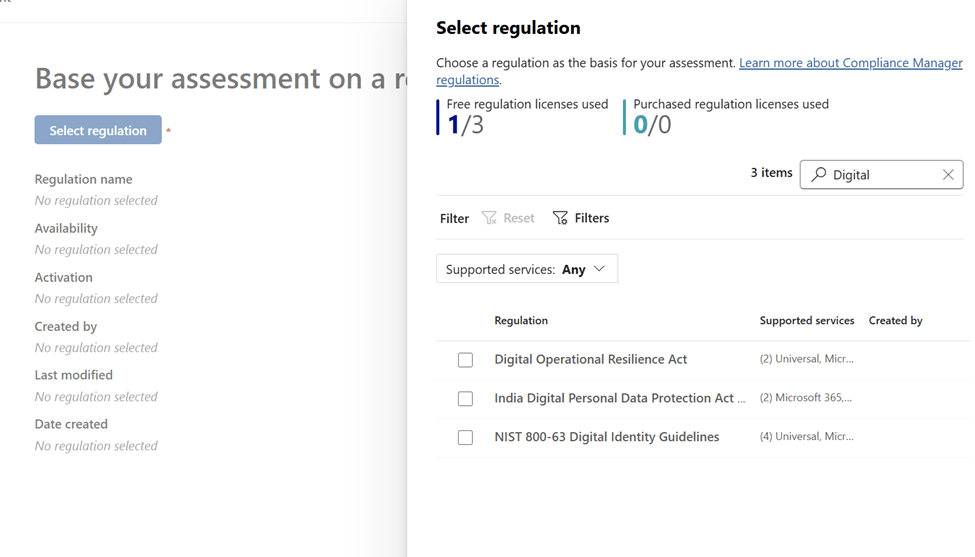
- Open Purview: Go to Microsoft Purview portal → Compliance Manager – Navigate to assessment – Select Regulation
- Find templates: Search for “Digital” under assessment templates. (I was not able to find with DORA :))