In today’s enterprise landscape, most applications are accessed through modern browsers like Microsoft Edge and Google Chrome, especially on Windows devices. While these browsers come with built-in security features, organizations must go a step further to enforce consistent and robust browser security policies across all endpoints.
If your organization uses Microsoft Intune, you have powerful tools at your disposal to configure and enforce browser security settings. In this blog, we’ll walk through 10 essential browser security controls you can implement using Intune’s Settings Catalog to enhance protection against web-based threats.
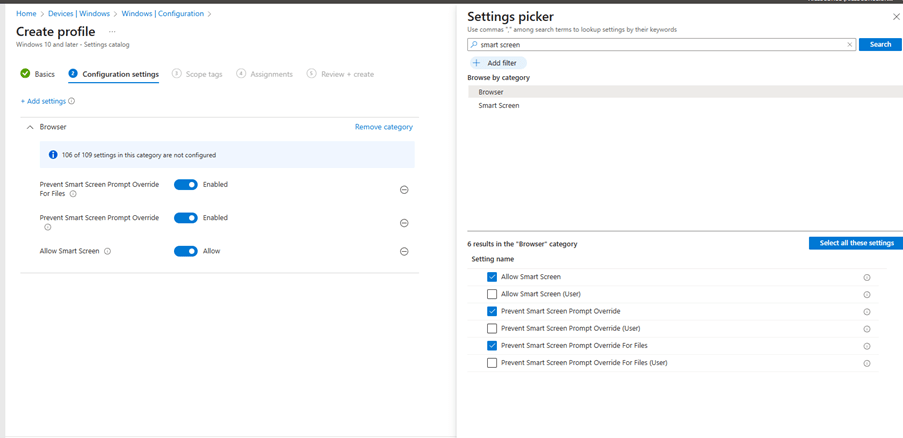
1. Enable Windows Defender SmartScreen
SmartScreen helps protect users from phishing attacks and malicious websites or downloads.
Recommended Settings:
- Enable Windows Defender SmartScreen
- Don’t allow SmartScreen warning overrides for unverified files
- Don’t allow SmartScreen warning overrides