Its been almost a year that Microsoft has announced the new release in Azure Sentinel which provides us the opportunity to integrate MS Teams related activities that are recorded in the audit logs to Azure Sentinel. Enabling this feature benefits organization where there is a separate SOC team monitoring and analyzing the security posture as an ongoing operational procedure.
We still have the Microsoft native cloud app security which benefits in creating the alerting mechanism for MS-Teams related activities.But with the Log Analytics and Azure Sentinel we can do a lot more than it can be done from the Cloud App Security. We can further fine tune the alerting, create workbooks and dashboards for Microsoft Teams related activities which will be useful for Teams Monitoring.
To start with this new feature ,we need to enable this new option to ingest Teams Data into Azure Sentinel Work Spaces. This article can be followed to start with connecting office 365 with the Microsoft Cloud native SIEM Azure Sentinel.
Navigate to Azure Sentinel Work Spaces – Select Data Connectors – Choose Office 365

Here we can see the new option for sending Teams Audit Logs to Azure Sentinel WorkSpace.

Once it is done after a while, we could see that the workspace have received the data types Office Activity (Teams)

Live Query Teams Monitoring :
When we navigate into the workspace we have the opportunity to fine tune and see the events that are written on the Audit Logs for Teams in a more refined way.
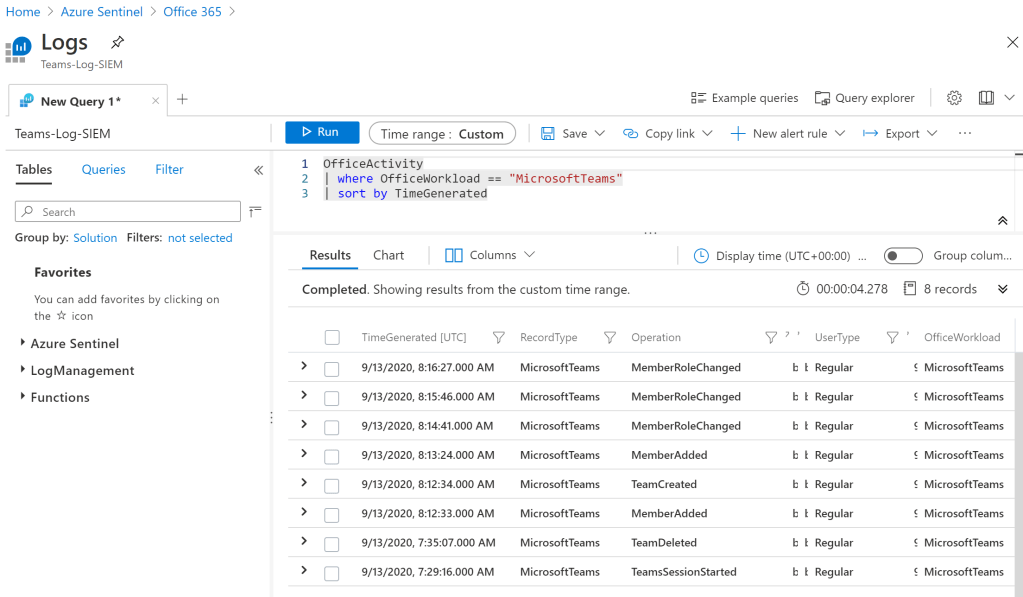
For instance to filter only Team creation can be checked from the workspace. This can be used for filtering even specific person and creating alert for them.
This helps the SOC Team for a live reactive analysis when any security incidents are reported for Teams related activities.
OfficeActivity
| where OfficeWorkload == "MicrosoftTeams"
| sort by TimeGenerated
| where Operation has "TeamCreated"
| where UserId has "sathish@exchangequery.com"
| project UserId,AddonName,TimeGenerated,RecordType,Operation,UserType,OfficeWorkload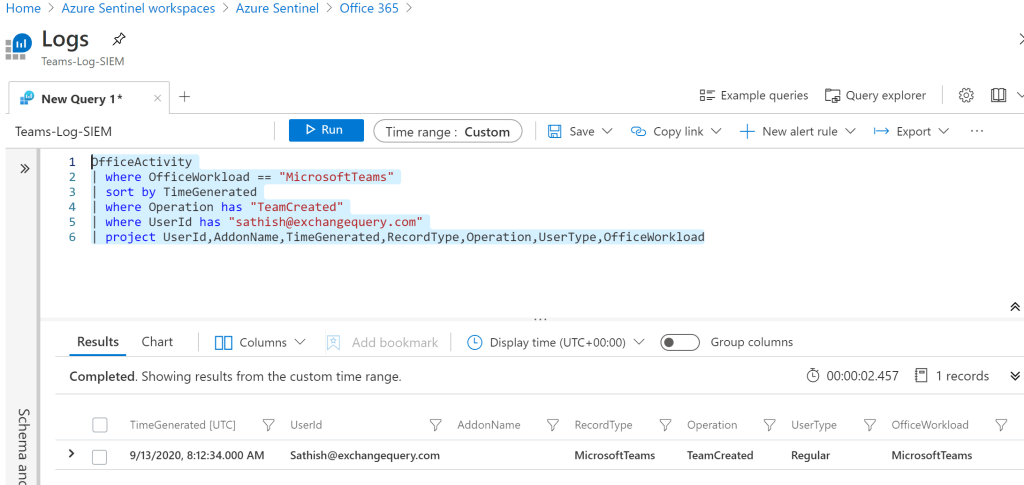
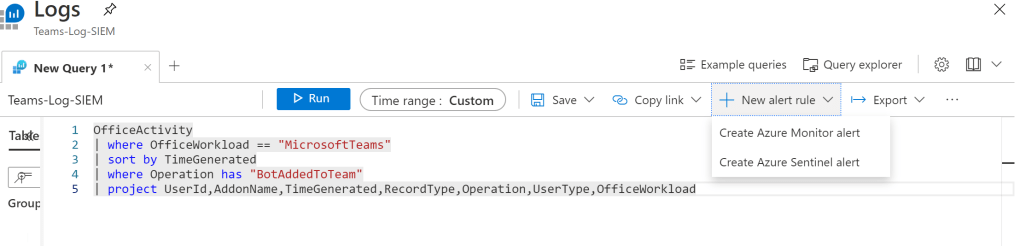
Create Alerting Mechanism : Azure Monitor or Azure Sentinel
In a real example we can create alerts and notify the SOC Team when a bot has been added to the Team.
OfficeActivity
| where OfficeWorkload == "MicrosoftTeams"
| sort by TimeGenerated
| where Operation has "BotAddedToTeam"
| project UserId,AddonName,TimeGenerated,RecordType,Operation,UserType,OfficeWorkload
To create the alert once after writing the query we have the new alert rule where there is an opportunity to create alerting mechanism in two methods. Create Azure Monitor Alert or Create Azure Sentinel Alert.
To experience the behavior selected the option Create Azure Monitor alert. Used the same Query. Alert logic and the time period is set for demo and can be defined based on the period and frequency that suits best for the monitoring.
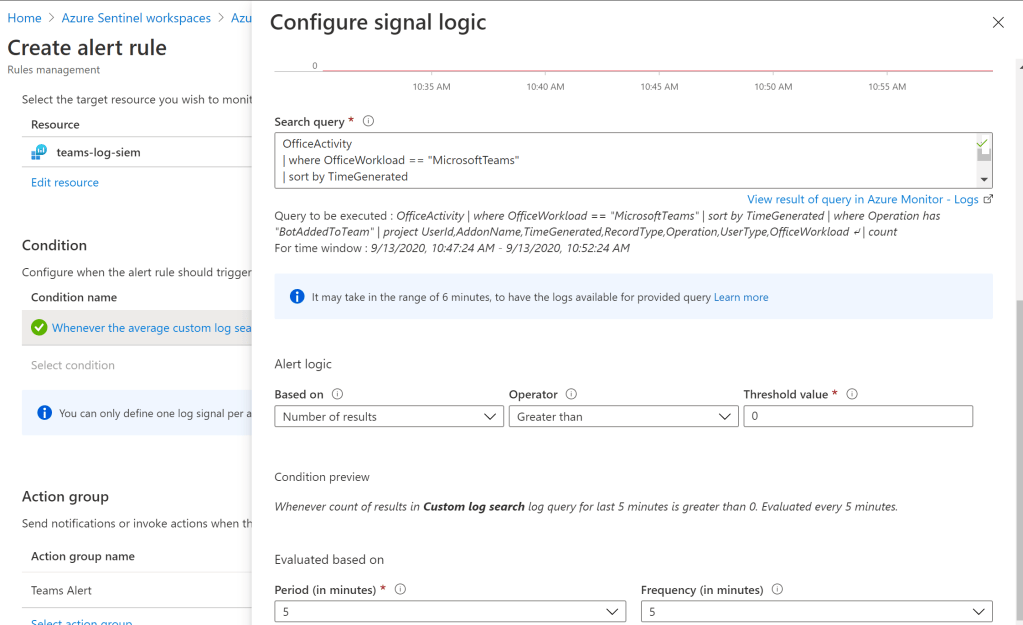
The action group can be selected to send this notification alert to a email addresses.
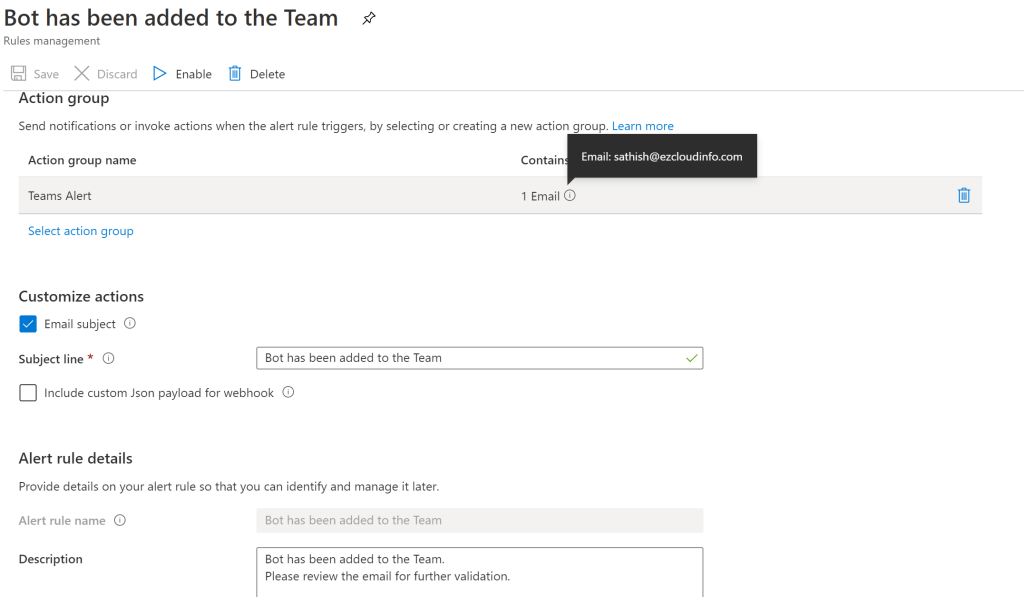
The notification type can be selected for other options like where ITSM can be chosen to trigger an incident for the same events.
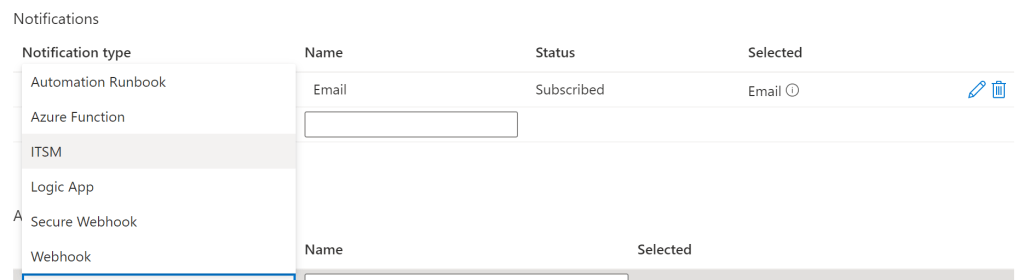
In our case email was selected and after few minutes tested by adding a bot and got the alert notified on email address.

Further information about the bots that have been added can also been seen.

Create WorkBooks and Dashboards:
Here we do have the possibility to create workbooks and dashboards for Ms Teams related activities. There is one template present by default for Office 365 and there is a item Teams Workload present over here which will help in creating a workbook for Teams.

The default workbook provides decent information on monitoring the Teams related activity.
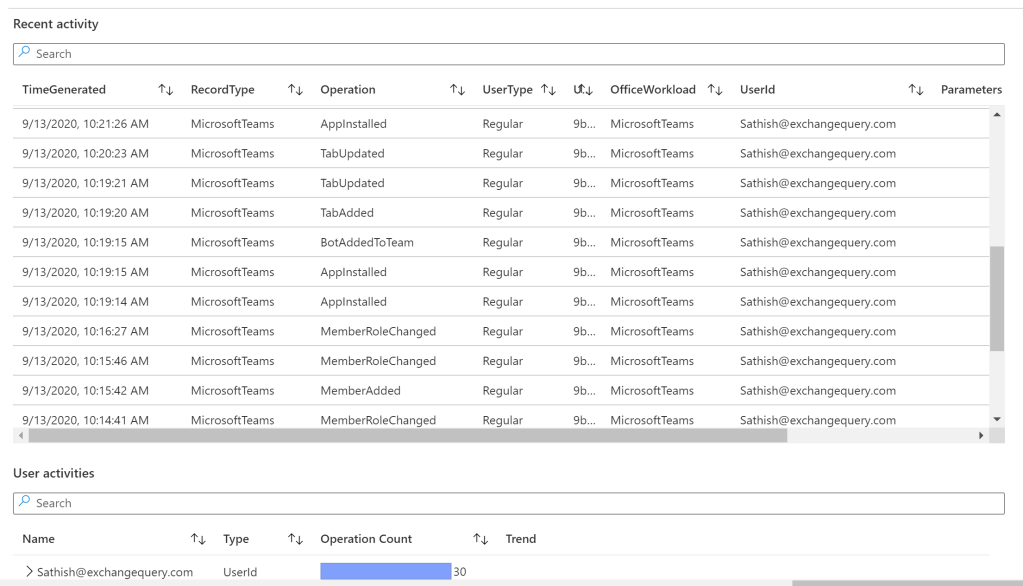
This will be a good start to create one dedicated work book for Microsoft Teams and pin them as a separate dashboards for Microsoft Teams related activities. I have also written post on creating Azure Monitoring Workbooks which can be referred for creating dashboards for Teams Activities.
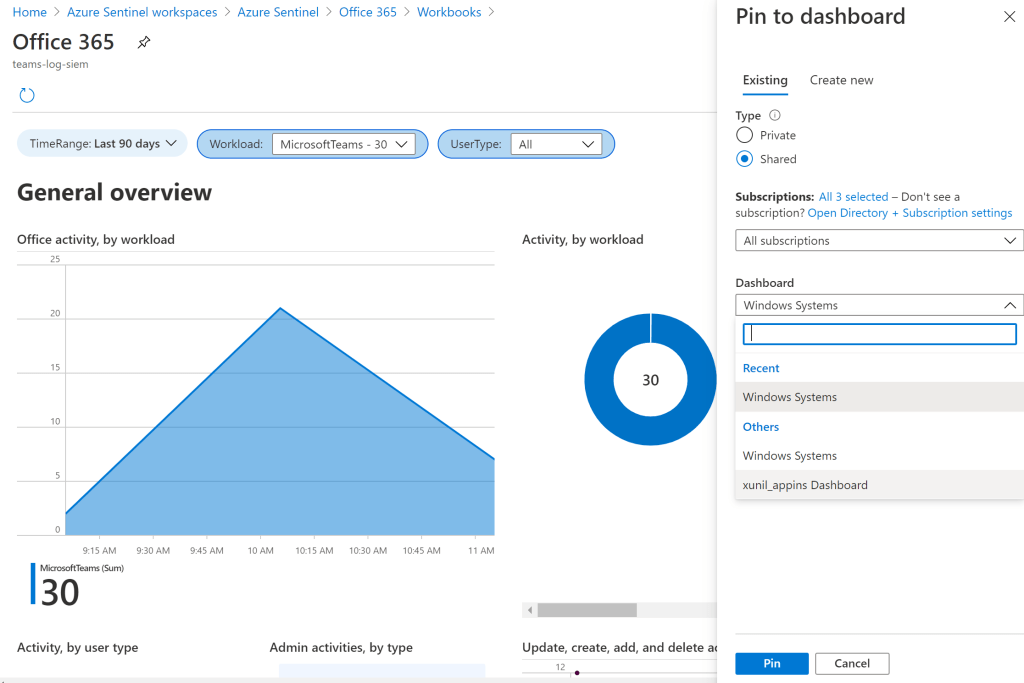
Microsoft Teams logs in Azure Sentinel is really a welcoming native cloud integration feature set where lot of organizations can be definitely beneficial in terms of actively monitoring the Teams Activities with no additional cost of investing on 3rd party SIEM integrations.
Regards
Sathish Veerapandian


Leave a comment