As we all know the basic authentication will be retired for Office 365 sooner and its high time for us to enforce Modern Authentication on all clients. When most of the organizations have already enabled Modern Authentication which is a good sign. However there are cases where the modern authentication cannot be interactive for the 2nd factor authentication ,needs some planning on those special cases and they have exceptions. For instance Room Systems they are having resource accounts with Teams Enabled and Exchange Online where these resource accounts cannot have modern authentication enabled with MFA like normal user accounts to approve for the 2nd factor authentication.
Post Microsoft Teams Room App version 4.4.25.0 we have the option to enable Modern Authentication on the devices capable of hosting Microsoft Teams Meeting. The account management of the Teams Room devices is set at the application level.
After turning on Modern Authentication on the Teams Room it leverages Active Directory Authentication Library (ADAL) to consume services Microsoft Teams and Exchange.
The modern authentication mechanism uses the resource owner password credentials authorization grant type in OAuth 2.0, which doesn’t require any user intervention. This is one of the key differences between how modern authentication works for user accounts versus resource accounts that are used by the Microsoft Teams Rooms application. Because of this, Microsoft Teams Rooms resource accounts shouldn’t be configured to use multi-factor authentication (MFA), smart card authentication, or client certificate-based authentication (which are all available for end users). Just enabling them modern authentication will trigger them the ROPC and grant the OAUTH 2.0 token. It uses the resource account to authorize the grant type and issue the OAUTH 2.0 Token. Can refer more over here to get more details on the authentication mechanism and plan them based on your environment.
So before enabling modern authentication make sure that the modern authentication must be enabled on the tenant level
In Office 365 Admin Center go to Settings -> Settings – > Modern Authentication

And you can turn off basic authentication completely after evaluation of sign-in reports or make exceptions for legacy applications based on the sign-ins until they are transitioned for the modern authentication support.

Enabling Modern Authentication on Teams Room Devices :
So the devices can be enabled for modern authentication by enabling the toggle which we can see from the Teams App version later than 4.4.25.0. This step could be easier when we are doing this for hand full of devices, however on a large scale enterprise deployments its better that we get this enabled via xml method from Microsoft Intune.
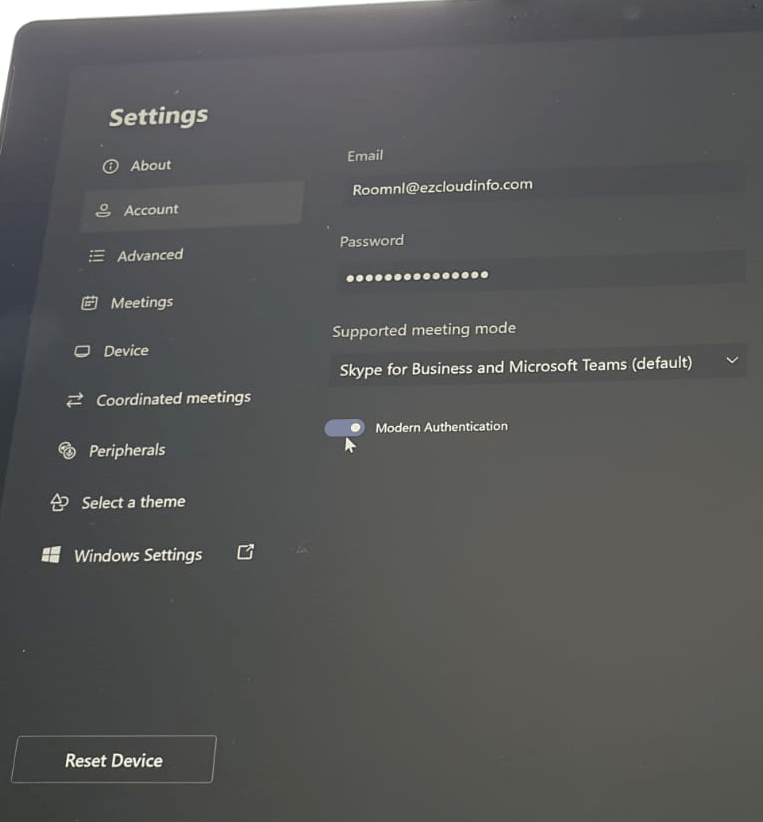
These XML files are located in a generic place for all Teams Room Devices
C:\Users\Skype\AppData\Local\Packages\Microsoft.SkypeRoomSystem_8wekyb3d8bbwe\LocalState
We have seen this similar scenario of XML deployment of changing the meeting mode in our Previous Blog
Using the same approach as mentioned in the previous blog use the below XML , Create a device configuration scripts and target them to the Room Systems.
$target = "C:\Users\Skype\AppData\Local\Packages\Microsoft.SkypeRoomSystem_8wekyb3d8bbwe\LocalState\SkypeSettings.xml"
$xml = "<SkypeSettings>
<ModernAuthEnabled>True</ModernAuthEnabled>
</SkypeSettings>"
$xml | Out-File -FilePath $target -Force
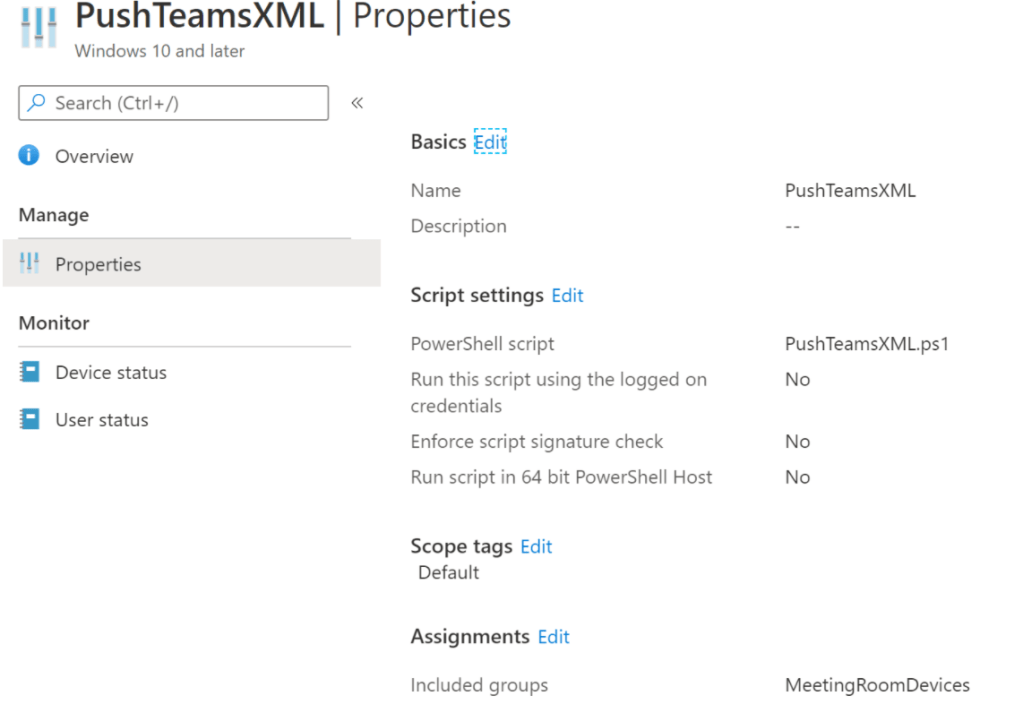
Once the device gets rebooted after its nightly scheduled maintenance tasks , it picks up the XML and finally enable the modern authentication on them.
Testing the modern Authentication:
We can login to the Azure AD Portal select Signins – Select the Client App Column – Choose User Sign-Ins (Non-Interactive) and select all the Legacy Authentication Clients.
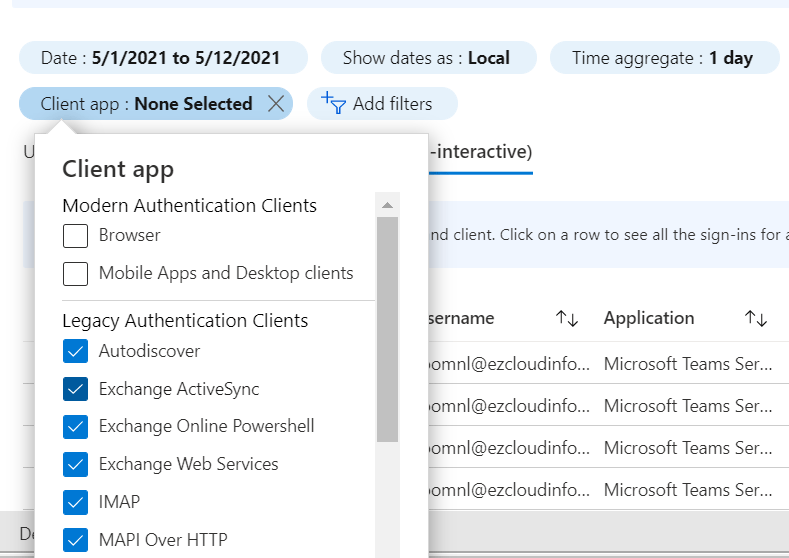
This is the previous state before modern authentication where the legacy method is successful for the test meeting room we are seeing below.

After enabling the modern authentication on all these devices and waiting for the logs to be available in the Azure AD Portal, when we filter for client app modern authentication type and they are fully in Modern Authentication.
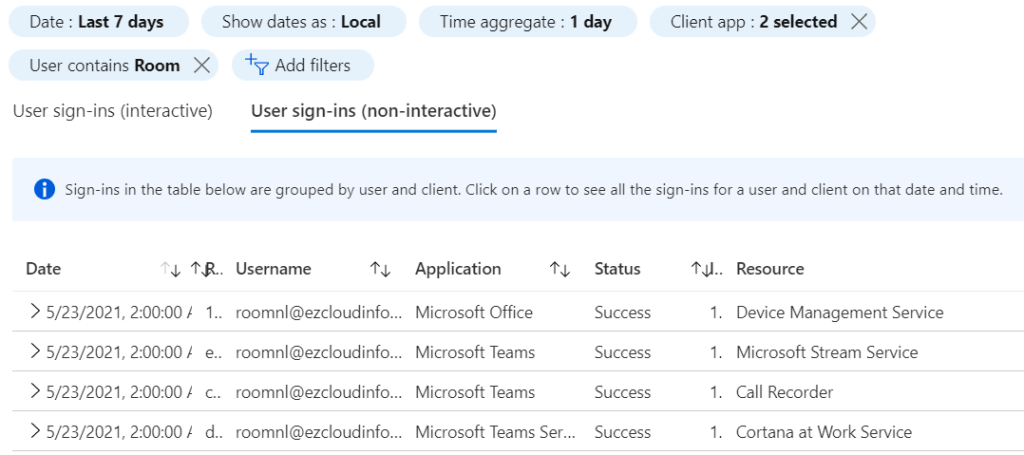

So once the above steps is completed the Room Systems will be enabled for modern authentication and they will no longer fail back to basic authentication as per this article. And as every environment is different in terms of federation & authentication mechanism scenarios its highly recommended to test this on small group of devices first, confirm if they can successfully sign-in to Teams and Exchange Online and upon successful validation can go ahead with enabling them on all room systems.
Regards
Sathish Veerapandian


Leave a comment