The Cisco unified messaging feature provides voice mail feature for Cisco Unity Connection client users. When this single inbox feature is enabled on Unity Connection, to the user mailbox in Unity Connection and then the mails are replicated to the user mailbox on Exchange the mails are replicated to the user mailbox on Exchange.
With Cisco Unified Messaging service users can access their Voice Mail in 2 ways :
Access their Voicemail from the Exchange inbox and listen them via computer speaker.
Directly from the phone interface.
Though there are multiple other options like text to speech, integrating with calendar options that can be done, but this topic focuses only on the voice mail part considering the article will become too lengthy if other components are explained.
Cisco Unified Messaging service supports the Following Exchange servers:
- Exchange on premise versions Exchange 2007, Exchange 2010, Exchange 2013 & Exchange 2016.
- Office 365.
Single Inbox :
Single inbox is the Feature Name in Cisco Unity Connection Manager
This supports the Synchronization of voice messages between the CUCM and Exchange/Office 365.Before we configure on Exchange the Single inbox feature in unity connection needs to be configured.
How it establishes connection with Exchange :
Unified Messaging Service is the component in CUCM which defines the connection and establishes the communication between exchange and CUCM for enabling this feature and delivering the voice mail to end user mailboxes.
Below is the High Level Architecture of how it works:

Components involved in them are :
Unity Connection Publisher.
Unity Connection Subscriber.
ExpressWay-E.
ExpressWay-C.
Microsoft Exchange.
Active Directory.
DNS records.
SSL Certificate for EWS/AutoDiscover.
Prerequisites from the Exchange Side :
The Unified Messaging service can connect to Exchange server in 2 ways:
1) We can select a specific Exchange server to communicate.
If we select a specific Exchange server, Unity Connection sometimes detects when we move mailboxes from one Exchange server to another, and automatically access the Exchange mailbox in new database and server. In scenarios ,When Unity Connection cannot detect the new mailbox, then we must manually update unified messaging services or unified messaging accounts. So its better not to go with this option.
2) We can make unity connection to search for Exchange Servers.
If we allow Unity Connection to search for Exchange servers automatically , then we need to give permissions from the Exchange servers through RBAC for the unity service account.
- One Unified Messaging Active Directory account needs to be created. This AD account will be configured on the Cisco Unified Messaging service to perform this operation.
- A dedicated RBAC role ApplicationImpersonation role needs to be created and assigned only to this account.
- Cisco Unified Messaging service uses Autodiscover and EWS protocol for this service to work. So all the end user clients needs to have access to this protocol
- Exchange server SSL certificate for EWS and Autodiscover needs to be installed on Cisco Unified Messaging service if require SSL is enabled for these 2 protocols on exchange server.
Network Requirements:
1)The Outlook clients & Cisco Jabber Clients should have perfect connection to EWS and Autodiscover which will be present by default.
2)The EWS connection between Unity connection and Exchange should be present.
3)The Autodiscover connection between Unity connection and Exchange should be present.
The default Unity Connection configuration settings is sufficient for a maximum of 2000 users and 80 milliseconds of round-trip latency between Unity Connection and Exchange servers.For more than 2000 users and/or more than 80 milliseconds of latency, we can change the default configuration as per cisco guide.
4)Unity Connection should be configured to use DNS, its recommend to configure Unity Connection to use the same DNS environment in which the Active Directory/exchange environment is publishing its records. If Split DNS configuration is used then all the required entries for Unity Connection needs to be configured on both the places.
Configuring Unified Messaging Services Account:
- This account will be used for unified messaging services to make it look generic.
- Do not create a mailbox for this domain user account. There are known histories where the unified messaging services not functioning properly with the mailbox.
- Do not add this account to any administrator group.
- This account must be enabled , with complex password and password never expire.
Create RBAC role for the dedicated mailbox account:
Run the below command in Exchange management shell for the created service account to get permission on exchange for searching the mailboxes.
New-ManagementRoleAssignment -Name rolename -Role:ApplicationImpersonation -User useraccount
Confirm Exchange 2016 Authentication and SSL Settings :
This part is very much required because Unity manager looks for EWS and Autodiscover for the service to work.
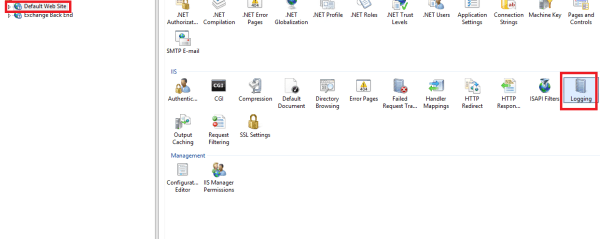
Authentication can be checked by logging into IIS manager in Exchange 2016 – Expand Sites – click Autodiscover and see the authentication and SSL settings
Check the same for EWS also.
Note: Unity Manager supports NTLM or Basic Authentication.
Depending upon the authentication setting we have on Exchange Autodiscover and EWS the same authentication must be used on the Unity manager.
If require SSL is enabled on both the protocols EWS and Autodiscover , then we need download SSL certificates from the Exchange server and install them on the Unity Connection server.
Below tasks needs to be completed in CUCM:
1) Create a new Unified Messaging Services in Unity Connection from Cisco Unity Connection Administration.
2) Upload the Exchange certificates to the Unity Connection server.
3) Enabled Unified Messaging for users in Cisco Unity Connection through Cisco Unity Connection Administration.
4) Users with Unity Connection mailboxes needs to have licenses assigned for this component through Cico Prime License Manager.
Rest detailed procedures on the above steps can be seen from the Cisco Articles for CUCM.
Thanks & Regards
Sathish Veerapandian