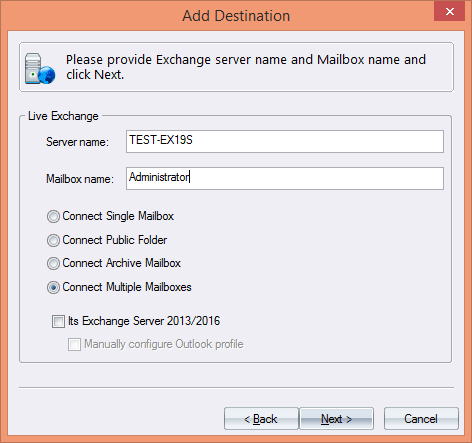
It can happen that we arrive at a point where the storage is not sufficient or reached the maximum level on the Linux Servers.
In this case we need to add a new physical disk ,create a physical volume and extend the existing logical volumes assigned on the Linux based application.
There are many ways of doing this job.
In this article we will have a look at one step to accomplish this activity.
Before assigning the new physical disk to the application we need to check the below values.
Open Putty session ssh to the Linux server and run the below commands in order.
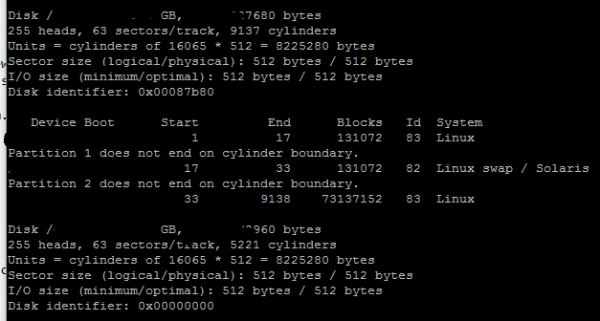
a. fdisk –l
This Fdisk command line utility is very useful in terms of creating space for new partitions, organising space for new drives, re-organizing an old drives and copying or moving data to new disks. It allows us to create a maximum of four new primary partition and number of logical (extended) partitions, based on size of the hard disk we have in our system.
In our case we use the above command to View all Disk Partitions their size and their name in Linux system
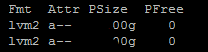
b. pvs
This reports information about physical volumes.
pvs produces formatted output about physical volumes.
In our case we use this to check the current physical volume size.
c. vgs
vgs command provides volume group information in a configurable form, displaying one line per volume group. The vgs command provides a great deal of format control, and is useful for scripting.
We are using this to display properties of LVM volume groups
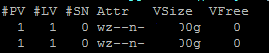
d. df
To get the VG name and LVNAME
df displays the amount of disk space available on the file system containing each file name argument. If no file name is given, the space available on all currently mounted file systems is shown.
In our case why we are using this is to check the current free space on the disks currently assigned.
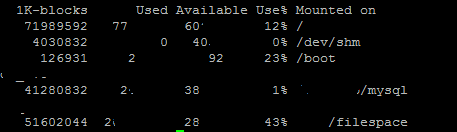
Also we get the current disk VG and LV names ,so that we run the LV extend on them after assigning the new disk in the next steps.
Now we need to follow the below steps after assigning the new disk
a. fdisk –l
Now after assigning the new disk we need to Compare the output from previous step fdisk output to find out the new disk name.
After identifying the new disk name we need to create the Physical Volume.
b. pvcreate /dev/sd<New Disk>
After we get the new disk name from the previous output we should run the above command with the new disk name.
Here we are actually choosing the newly assigned physical volumes that will be used to create the LVM.
We can create the physical volumes on the linux system using pvcreate command.
c. lvextend –lvresize +200GB /dev/VGNAME/LVNAME
lvresize can be used for both operations (shrinking and/or extending) The lvresize will resize only the virtual volumes.
In our case we are using this command utility to the newly added space to resize the existing LVs.
There are few other options to extend the logical volume. By using the above command syntax we are reserving additional 200 GB space on this physical disk.
This 200 GB free space can be extended any time online to any LV’s without need for a reboot or bringing down the application if we run out of space for the file system in future.
So It is always important to include the plus (+) signs while resizing a logical volume.
If we don’t do this then we are setting a fixed size for the LV instead of resizing it.
d. Finally after all the above steps are done we can run pvs
After running PV’s we can Compare the output from previous step output of PVS;
After the comparison the we need to extend new volume group by the below command.
resize2fs /dev/sd<newdisk>
Note:
Its very important to note that you need to understand how the LV’s , PV’s & VG’s are created and assigned on the Linux application.
Also do this only if you have worked and having knowledge on the Linux systems.
If you are not sure on this its always better to perform this action with Linux Admin.
Thanks & Regards
Sathish Veerapandian
MVP – Office Services & Servers